Phishing Example
Below is a phishing email that was sent around WKU. These emails can be very convincing but are NOT sent from WKU. They are an attempt to steal your account credentials. There are usually a few signs that give these away as a 'phishing' attempt, explained below.
Example Phishing Email
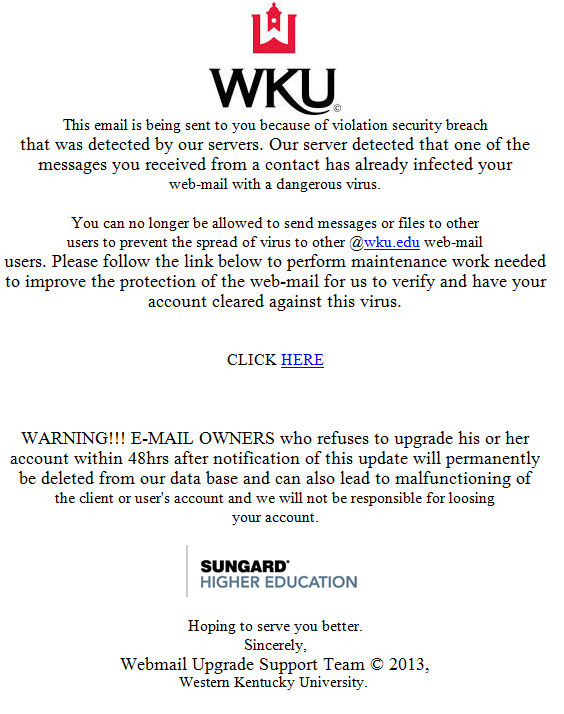
How to Identify This as a Phishing Scam
#1
A good sign that this is a phishing attempt is the link itself, it leads to a form that doesn't run on WKU's web servers (wku.edu) and only asks for your account NetID and password (called access code):
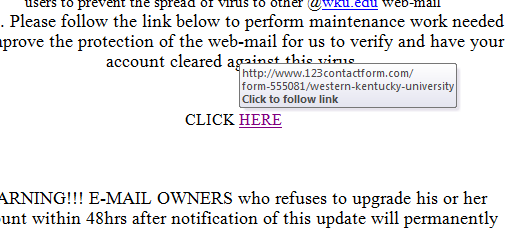
Do not click links if they do not go to a wku.edu page.
#2
You can see the link from the first image goes to a 123contactform.com site containing the form below. WKU will never ask you for your account password in a form like this, or any other way.

Do not fill out forms like these, reach out to the service desk if you are not sure.
#3
Another good sign that this is a phishing attempt is the warning at the bottom of the message.
This kind of warning with an unreasonably short window for response and harsh penalties for non-compliance is intended to scare you into filling out the form as quickly as possible without considering the source or truth of the message.
Note also the poor phrasing and misspellings in the entire email.
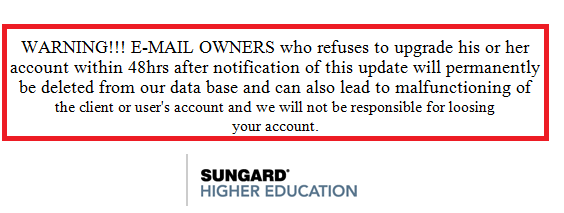
Warnings like this are a good indication of a phishing scam email, look out for them.
Need Assistance?
The WKU ITS Service Desk is here to help. Give us a call, chat with a representative online, use the Self-Help Knowledge Base and more.
Some of the links on this page may require additional software to view.

